30+ network security zones diagram
Organizations must examine their. Security Zones let you be confident that your resources in Oracle Cloud Infrastructure including Compute Networking Object Storage Block Volume and Database resources comply with.

Ot Industrial Cybersecurity Solutions Opswat
Zone Segmentation In A Office Network Local Network Security Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple.
. A zone can have sub-zones. A conduit cannot have sub-conduits. About Security Zones Each zone has an associated security level.
Enter a name for the Security Zone. A network security zone can contain a single IP address or any combination of IP addresses and subnetworks. The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils cliparts shapes icons and connectors to help you succeed in designing.
Below we share some practical rules that will be useful. It helps to ensure the protection of valuable information as it. A network security diagram maps out the security methods implemented to protect an organizations assets.
A zone can have more than one conduit. Ad Templates Tools Symbols For Easy Network Diagrams. The Network Security Zoning is an unclassified publication issued under the authority of the Chief Communications Security Establishment Canada CSEC.
A network security diagram maps out the security methods implemented to protect an organizations assets. It helps to ensure the protection of valuable information as it is stored. The Security Zone window opens.
Start by drawing the box that you want to represent the area. Duplicate that box Control-D and rotate Control-R and then make it a bit smaller with your mouse. Ad Easily Find The Network Security Systems Youre Looking For w Our Comparison Grid.
Find the Best Network Security Systems That Will Help You Do What You Do Better. Default firewall rules are created for all predefined. In the Objects bar F11 click New More Network Object Security Zone.
All of the IP addresses in a security zone must have the same security label. The network perimeters that define these zones provide protection based on security requirements and business communications needs. To create a Security Zone.
The security level represents the level of trust from low 0 to high 100.
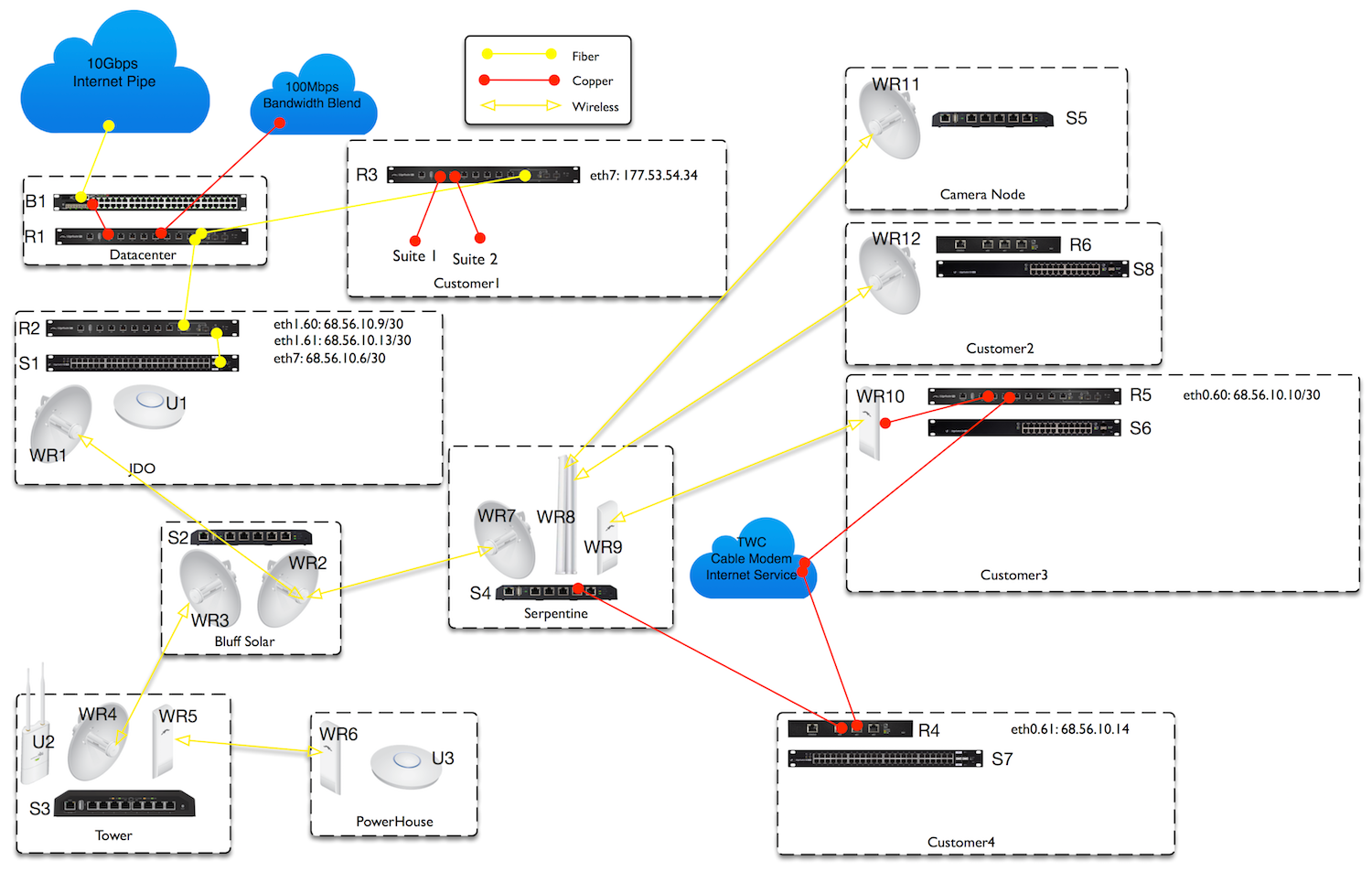
Routing Vlan Config Port Forward Help Suggestions Needed Ubiquiti Community

Ot Industrial Cybersecurity Solutions Opswat
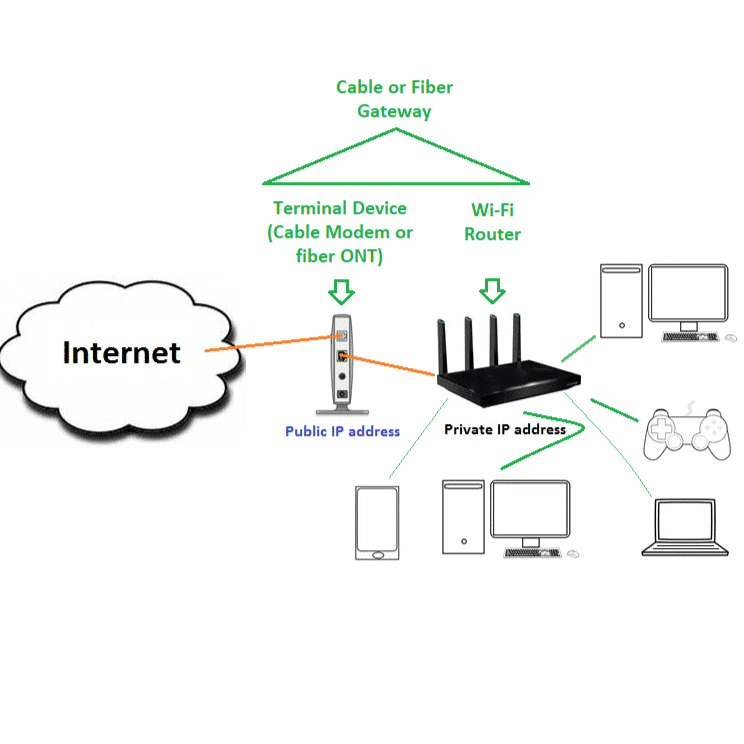
Home Wi Fi Network 101 Beginners Best Tips Dong Knows Tech

Gcp Reference Architecture Vmware Tanzu Docs
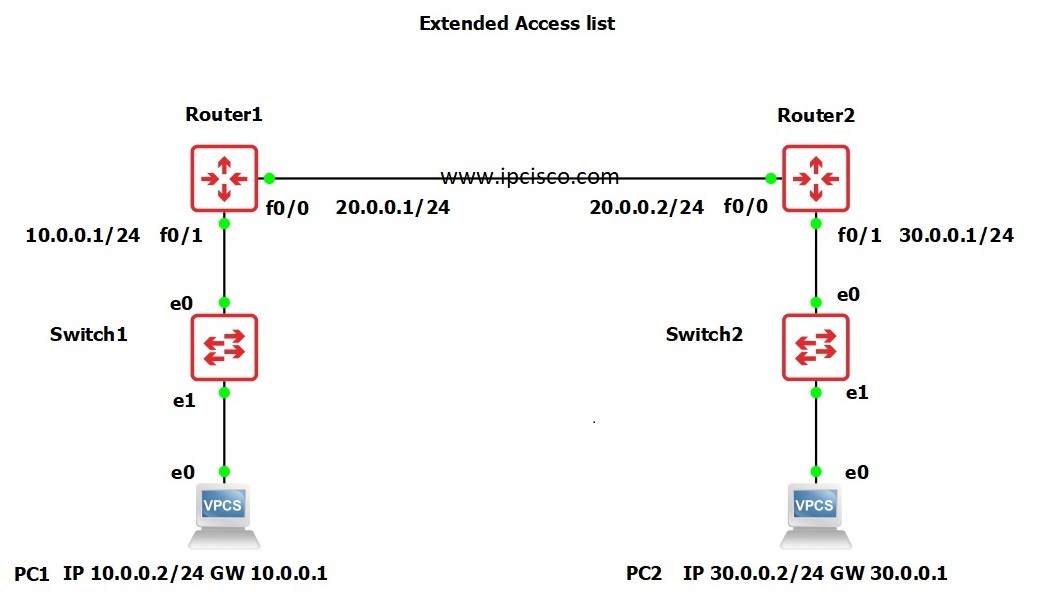
Extended Acl Cisco Configuration On Gns3 4 Steps Ipcisco

Ot Industrial Cybersecurity Solutions Opswat

Requirements For City Dot Functions By Benjamin De La Pena Medium
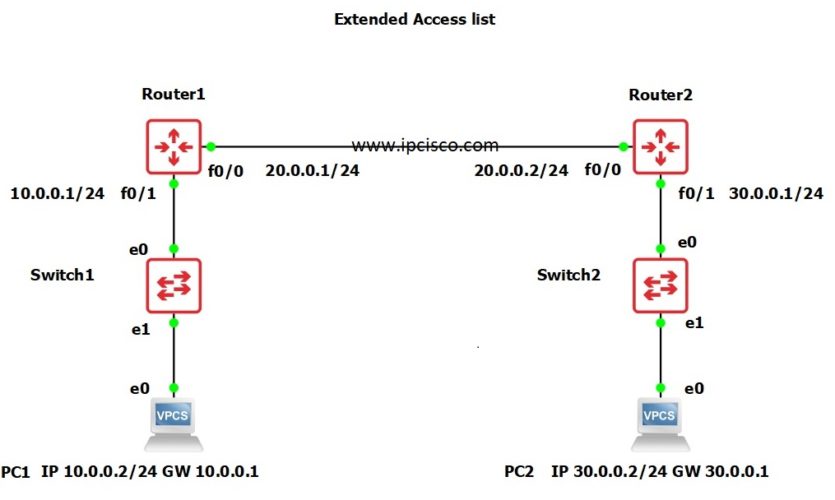
Extended Acl Cisco Configuration On Gns3 4 Steps Ipcisco
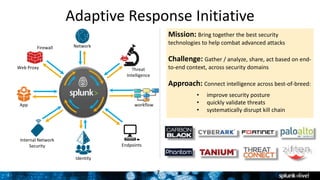
Splunk For Enterprise Security Featuring Uba Breakout Session

Cisco Network Diagram Network Organization Chart Computer Network Cisco Networking Networking
Blog The Art Of Network Engineering

Vyos On Nutanix Ahv Vyos
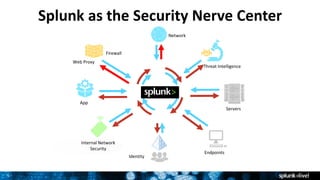
Splunk For Enterprise Security Featuring Uba Breakout Session

Cheat Sheets Packetlife Net Computer Programming Computer Technology Computer Network

Multi Access Edge Computing Standards Combine To Offset Security Threats Embedded Com
2

Threat Analysis Unit Asean